- Call Us: +966580845046 Call Us: +201092472218
- Email us: [email protected]
- Working Hours: 08:00-16:00
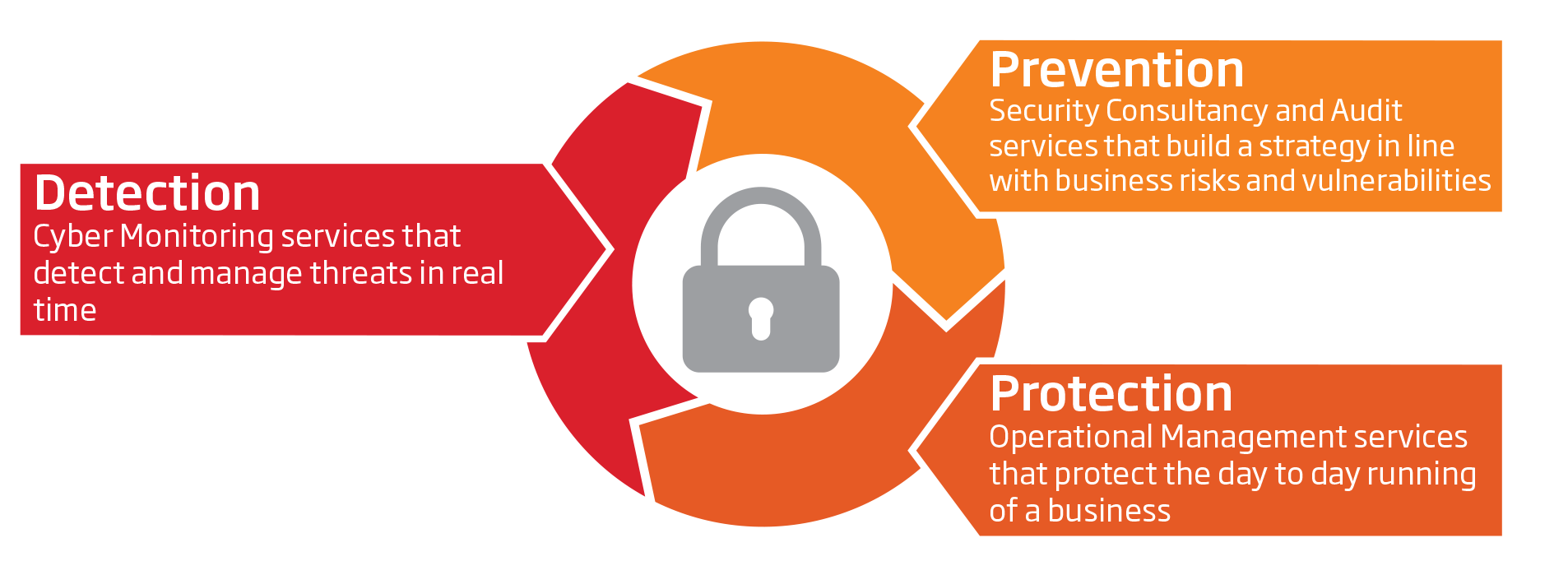
Penetration Test
There are different types of penetration testing that we offer you. We would be happy to explain every single type of penetration testing to you. External pentest This approach is often chosen. Companies want to know how secure they are against external attacks. Internal pentest If the company to be tested is of a certain size (from around 50-100 employees), internal IT security factors gain in value. So trust in one’s own employees is no longer guaranteed by a family environment. The risk of an internal attack increases with the size of the company. A goal is defined for an internal IT penetration test. This can be, for example, testing all internal systems or checking security against internal attackers in the event of certain break-in scenarios. Priorities, such as theft of the hashed passwords on the domain controller, can be set.
Our team previous Penetration Testing experience
We are experienced in the Part of PCI-DSS Testing and and were involved in a lot of Bank Penetration Testing including the PCI-DSS Implementation
As an Example we have tested the following Banks:
– Austrian Bank (without mentioning the Name for privacy agreement)
– Abu Dhabi Commercial Bank – Egypt
Our team previous experience in security architecture review
Our IT-Security Experts were working as IT-Security Engineers so they have experience in implementing and reviewing the internal and external Architecture for example Firewalls, Switches, Routers, etc.
One of the biggest Companies in Austria (NOVOMATIC AG)
They were responsible for internal and external Penetration Testing for the whole Company including the Head Quartier etration Testing for Companies in Poland, Germany, and other Countries
Penetration Testing Fields: Web Application, internal & external Infrastructure, Firewall Bypassing, etc.
We used the F5 Big-IP Firewalls and were responsible for Firewall Reviewing, configuring the Firewalls, setting the Web Application Protection settings and parameters, etc.
Configuring the DMZ (Demilitarized Zone) to secure the internal and external IT Environment.
Previous experience in WAF (preferably F5)
As mentioned we used the F5 Big-IP including Configuration, Setup, Penetration Testing, etc. So we have strong knowledge of F5 Big-IP Technologies.
Assigned CVEs
Furthermore our Team was able to identify 13 Zero Day Vulnerabilities in a Software and got assigned 13 CVEs.
All of them are HIGH Vulnerabilities except one MEDIUM.
You can search for the Vulnerability and request a Proof of Concept if you like.
CVE-2023-0787
CVE-2023-0791
CVE-2023-0564
CVE-2023-0565
CVE-2023-0566
CVE-2023-0572
CVE-2023-0794
CVE-2023-0793
CVE-2023-0792
CVE-2023-0790
CVE-2023-0789
CVE-2023-0788
CVE-2023-0786
Provide references (3) for previous client
We did countless Penetration Tests for worldwide big Companies and identified Security weaknesses and several critical and high Vulnerabilities in Bug Bounty programs.
o Allow us to list some of our Penetration Test clients and Bug Bounty Program achievements. We want to mention that we have many other Clients but due to the amount we can not list all of them (if you need any Hall of Fame we can give you the PDF or E-Mail acknowledgment):
– UK Ministry of Defense (Hacker Coin received as Thank you)
– NAMARIQ
– USA – sim card company (with payment system)(Penetration Test service almost for 1.5 years and still)
– Sparkasse – Austrian Bank
– Abu Dhabi Commercial Bank – Egypt (API Penetration Testing)
– Austro Arab Chamber of Commerce -Austria OPEC – Austrian Website
– Austrian Federal Railways
– SAP – 3 identified Vulnerabilities and listed on their Hall of Fame
– United Nations – UN
– Government Technology Agency of Singapore (GovTech)
– MTN Group (on Hackerone received)
– UK Government
– U.S. Department of State 7x Vulnerabilities -> Multiple Vulnerabilities submitted (Stored XSS, SQL Errors, SQL Injection, etc.)
– NASA
– INDIAN GOVERNMENT -> Stored Cross Site Scripting (XSS)
– PHILIPINES GOVERNMENT -> Reflected Cross Site Scripting (XSS)
– CERT-EU Computer Emergency Response Team (CERT-EU) for the EU institutions
– SCOTTISH GOVERNMENT -> Multiple Vulnerabilities
– NEW ZEALAND GOVERNMENT
– Huawei -> stored XSS and File Upload Restriction Bypass
– Drexel University of Texas of Austin – HP (Hewlett Packard) 2x Vulnerabilities
– Lego (E-Mail acknowledgment)
– Lufa (https://montreal.lufa.com/en/security)
– Radica Software
– University of Cambridge (PDF File Acknowledgment)
– stkkr.nl (Website Hall of Fame)
– Nokia
– Oracle (E-Mail and Hall of Fame listed on their Website)
– Kuula (Hackerone)
– Bosch
– Lenovo (acknowledgment via E-Mail)
– Philips
– Technische Universität Dresden (Germany University) BANK Bonhote – Switzerland Penetration Test performed
